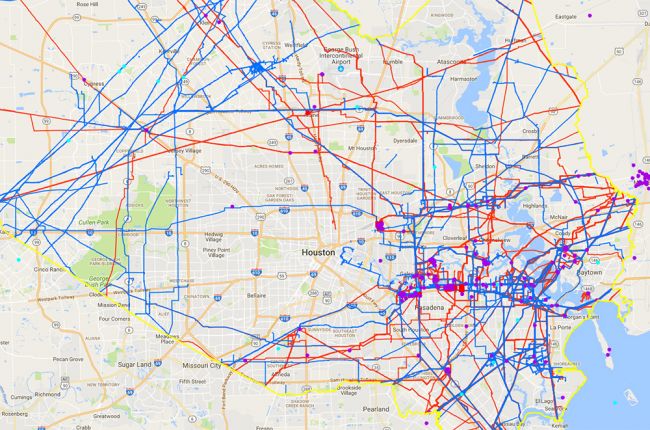
The National Pipeline Mapping System (NPMS) Public Viewer
from the Pipeline and Hazardous Materials Safety Administration allows
users to view pipelines and related information by individual county for
the entire United States. The map includes:
- Gas and hazardous liquid pipelines
- Liquefied natural gas (LNG) plants
- Breakout tanks (tanks used for storage or flow relief)
- Pipeline accidents and incidents going back to 2002
Users can click on individual pipelines to find operator
information and contact details, pipeline status and length, and the
commodity being carried by the pipeline. For accidents, available
information includes the date of the accident, the name of the operator,
the material released, the total volume lost and recovered, and the
cause of the accident.
The map does not include gathering or distribution pipelines, so it
does not show pipelines that deliver gas to people's homes. The minimum
accuracy of the pipeline information on the viewer is +-500 ft. For
higher precision in locating pipelines, more information, and contact
details for the NPMS, visit the NPMS FAQs.
Click here to access the interactive map.
https://www.americangeosciences.org/critical-issues/maps/interactive-map-pipelines-united-states
I wrote this message last night but chose to send it today because I wanted to be considerate of your Saturday.
Your comment about when we are splitting the T mobile bill speaks volumes of how you do not care about us.
Since
we've been in Charleston for a year, we NEVER have never made you care
about us or our well being. Never told you or complained about our
situation. I asked you to send me the MRE meal supply November of last
year only because we actually needed the food. We had just moved in and
it took 2 months to get back on our feet from CA...to pay for a
t-mobile/rent/expenses & life here. Michael had to literally take
food from a grocery store because that's how little $ we had.
Our
past experience from Chile to Texas, I put it all on myself and made ME
responsible for it. But let's be clear if it INDEED worked out you
would have benefited from it fully not just us. We did the work and you
would be equitably compensated as 50/50 partners (Michael & Jess 50%
/ Jr. 50%). You demanded that split. As we evolved and we found out my
truth, you always believed you were entitled to be the "golden caboose".
I am NOT living my truth on the outside yet so you don't belive my
truth is real. We have nothing to seemingly offer (apartment / car or
anything shiney) so we don't matter.
What you gave in the past was NOT just purely for the goodness in your heart.
I
reiterate here that we have not made you care about us since being here
in CHS. You are on your own path and are use to receiving full support
from the Government.... so you are used to being "taken care of" and not
responsible for anyone but yourself.
I
don't ask for anything from you.You don't care about what we have or
don't have. Or how anything affects us, re: your insensitive comments. I
count my blessings but I never tell you how it's been a struggle or how
much pain I'm in.
Mean while the past 10 years, your pain was ALWAYS my pain. And don't just say it was the past 6 years. Especially
Pre-book.
Above
all, you totally exempt ME being anything of significance...forget
about even mentioning the G word. I am NOT the living G in your life.
You care more about Heinz the dog then me.
So what, if you have to go without olive garden or drinks with friends to help pay the T mobile Bill.
We don't have a reoccurring salary.

HAVE YOU LOST YOUR HARD EARNED FUNDS TO THE WRONG HANDS?
ReplyDeleteMEET THE PROFESSIONAL HACKERS FOR HIRE TODAY.
⏱️ 3min Read
�� Hiring a professional hacker has been one of the world's most technical valued navigating information.
Regarding:
•Recovery Of Lost Funds,
•Mobile Phone Hack.(Catching A Cheating Spouse).
•Credit Score Upgrade,
VARIOUS HACKTIVITIES via
leroysteckler@gmail.com
High prolific information and Priviledges comes rare as it has been understood that what people do not see, they will never know. The affirmative ability to convey a profitable information Systematically is the majoy factor to success.
Welcome to the Global KOS hacking agency where every request on hacking related issues are fixed within a short period of time.
When you wonder “which hacking company should I hire, the first aspect that should concern you is Sincerity. Secondly, Rapid response. Clearly, you want to embark for services that povides swift response, With our astonishing Hackers, you will be glad to find out that our services Implies precision and action.
This post is definitely for those who are willing to turn their lives around for the better, either financial-wise, relationship-wise or businesses.
The manual Operation of this hackers is to potentially deploy a distinguished hacking techniques to penetrating computers.
If your shoe fits in any of the services below, you will be assigned to a designated professional hacker who is systematically known for operating on a dark web V-link protocol.
Providing value added services to clients as a hacker has been our sustaining goal.
Are you faced with cyber challenges like
��Recovery of lost funds:✅(BITCOIN INVESTMENTS, BINARY OPTIONS, LOAN AND TRADING FOREX WITH FORGERY BROKERS.) ��️I would try my possible best to shortly explain this in particular.
This shocking study points to one harsh reality we all face today. It saddens our mind when client expresses annoyance or dissatisfaction of unethical behaviours of scammers. We have striven to make tenacious efforts to help those who are victims of this flees get off their traumatic feeling of loss. The cyber security technique used to retrieving back the victims stolen funds is the application of a diverse intercall XX breacher software enables you track the data location of a scammer. Extracting every informations on the con database. Every information required by the Global KOS would be used to tracking every transaction, time and location of the scammer. This is acheived using the systematic courier tracking base method•
However, there are secret cyber infiltrators called brokers and doom. The particular system used by this scammers permeates them to manupulate targets digital trading system or monetary fund based accounts. Strictly using a dark web rob to diverting successful trades into a negative outcome. This process bends to thier advantage while investors results to losing massive amount of money. An act of gaining access to an organization or databased system to cause damages. We have worked so hard to ensure our services gives you a 100% trading success to recover all your losses•
�� HACKING A MOBILE PHONE:.✅ Do you think you are being cheated on? Curious to know what your lover is up to online? This type of hack helps you track every movement of your cheater as we are bent on helping you gain full remote access into the cheater's mobile phone using a Trojan breach cracking system to penetrate their social media platforms like Facebook, whatsapp, snapchat etc.
The company is large enough to provide comprehensive range of services such as•
• Email hacks��
• Hacking of websites.��
• Uber free payment hacks.��
Our strength is based on the ability to help fix cyber problems by bringing together active cyber hacking professionals in the GlobalkOS to work with.
Contact:
✉️Email: theglobalkos@gmail.com
Leroysteckler@gmail.com
®Global KOS™
2020.
On the other hand she might have found a guy who she is seeing so i feel you should hack the phone because some women are mischievous they keep secret and find a way to move out of this i feel there is someone she is seeing so you can contact WWW.HACKINTECHNOLOGY.COM and see so you can have a concrete reason so its up to you just a piece of advise from a rea life similar problem
ReplyDelete